uint64_t Pyro_AssetBundleManager_AssetBundlesLoader__GetAssetBundleOffset(
System_String_o *platform,
System_String_o *path,
const MethodInfo *method)
{
System_Text_Encoding_o *ASCII; // x19
System_String_o *v6; // x0
__int64 v7; // x0
__int64 v8; // x9
unsigned __int8 v9; // w8
_BYTE *v10; // x10
__int64 v11; // x11
__int64 v12; // x12
ASCII = System_Text_Encoding__get_ASCII(0LL);
v6 = System_String__Concat_121532840(platform, path, 0LL);
if ( !ASCII
|| (v7 = ((__int64 (__fastcall *)(System_Text_Encoding_o *, System_String_o *, const MethodInfo *))ASCII->klass->vtable._18_GetBytes.methodPtr)(
ASCII,
v6,
ASCII->klass->vtable._18_GetBytes.method)) == 0 )
{
sub_2DA6564();
}
v8 = *(_QWORD *)(v7 + 24);
v9 = 0;
v10 = (_BYTE *)(v7 + (int)v8 - 1 + 32);
if ( (int)v8 >= 1 )
{
v11 = (unsigned int)*(_QWORD *)(v7 + 24);
if ( (unsigned int)*(_QWORD *)(v7 + 24) )
{
v9 = 0;
v12 = 0LL;
while ( v11 != v12 )
{
v9 += *(_BYTE *)(v7 + 32 + v12);
if ( (v12 & 3) == 0 )
v9 += *v10;
if ( v11 == ++v12 )
goto LABEL_10;
}
LABEL_12:
sub_2DA656C();
}
}
LABEL_10:
if ( !(_DWORD)v8 )
goto LABEL_12;
return (unsigned __int8)*v10 * (unsigned int)v9 % 0x3E8 + 1000;
}
这里贴一段代码是计算偏移量的应该是(FeakHead)
还是没有找到下载的MasterData和第一个ab包
https://asset.lecisxqw.com/amgameasset/Stg/AssetBundles/Android/9A188D7BF0BF119DE38B57A44DF3A917.ab
的解密逻辑(恼
这个偏移量计算函数在
void Pyro_AssetBundleManager_AssetBundlesLoader__LoadAssetBundleFlow_d__41__MoveNext(
Pyro_AssetBundleManager_AssetBundlesLoader__LoadAssetBundleFlow_d__41_o *this,
const MethodInfo *method)
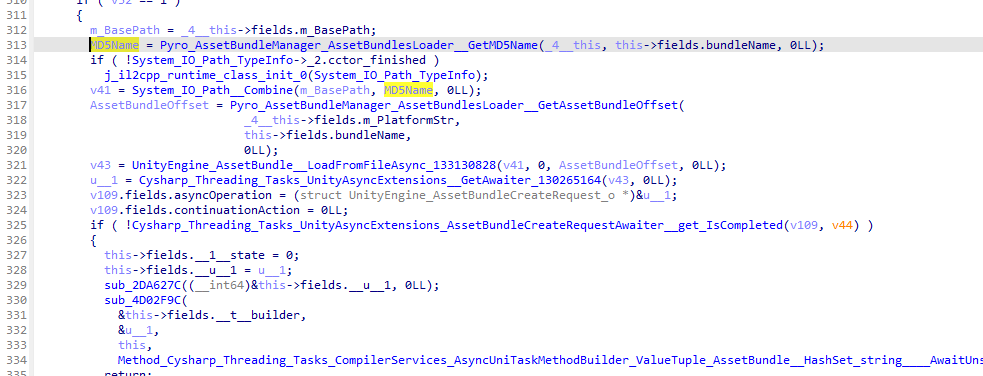
被调用(使用1.0版本做的分析新版1.01懒得再重新分析了)
从代码中可以看到对文件名进行了md5加密而下载的文件命名也确实是md5作为文件名
图随便截的函数中一个获取MD5的地方这个函数足足有715行代码。。。应该是AssetBundle加载的核心